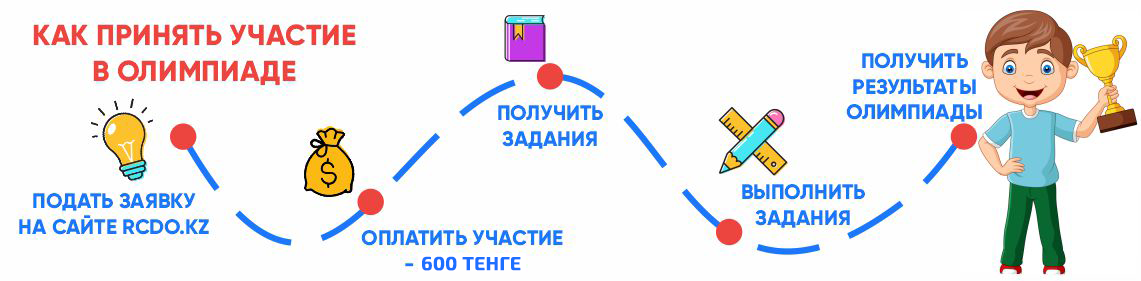
Wi‑Fi remains exposed to two practical attack surfaces: Evil Twin access points that impersonate trusted SSIDs and weak keys/misconfigurations that enable offline guessing. This expanded literature review (2015–2025) applies a PRISMA‑style method and synthesizes evidence from protocol breakages (KRACK, Dragonblood, Kr00k, FragAttacks), Evil‑Twin detection methods, toolchains/datasets, and policy/standards. We translate these results into a deployable audit system and provide richer evaluation visuals (evidence map, ROC, confusion matrix), aiming for high precision with low false positives on commodity hardware.
Публикации
Похожие материалы
- Nuclear energy and radiation: salvation or health risk?
- Digitalization in Kazakhstan
- Research paper on a topic: Is it wisely to follow all Kazakh traditions in a modern world?
- Word lists for Spelling Bee Contest
- The farming and environment. Is agriculture and cattle more dangerous than useful?
- Is it possible to combine orphanages and nursing homes in Kazakhstan?
- Internal computer devices
- Describing a favorite book
- Is it worth modifying the genes of human embryos, even if it is not ethical?
- Тесты по подготовке к ВОУД
Наши олимпиады